Enterprise - Implementing Coviu with Azure SSO in your Organisation
This article explains the steps taken to integrate Coviu into your Azure Single Sign-On (SSO) system.
Last updated: May 2024
This article is aimed at SSO System Administrators.
You will need Coviu Platform Administrator access to undertake the following configuration activities or, undertake these actions in conjunction with your Coviu Platform Administrator.
On this page:
- Introduction
- What do we need you to do?
- How do I get to the SSO self-help portal in Coviu?
- What config items do I need?
- FAQ's for the SSO Administrator
- FAQ's for the end user
- More support options
Introduction
Coviu now has a self-help SSO configuration interface built in to your Enterprise platform. These instructions will guide you on how to access and implement Coviu SSO using the interface.
What do we need you to do?
Create a new application registration!
The below instructions should only be used as a guide. Your SSO Administrator will know the specific steps required to create a new application registration within your system so the instructions below should be used within that context.
- Sign in to your Azure Portal
- Go to Azure Active Directory
- Under Manage, click App Registrations
- Click the New Registration option
- Provide the following details:
- Name: Coviu (or your preferred naming convention)
- Supported Account Types - this setting will depend on your organisation setting, but will generally be the Single Tenant option to only allow authentication by users in this Active Directory tenant
- Redirect URL:
- Select Web
- https://<your coviu sub domain here>/sso/callback?domain=<your chosen login email domain here> e.g: https://telehealth.mycompanyname.com.au/sso/callback?domain=mycompanyname.com.au
- NOTE: Your Coviu sub domain is the domain you provided to host the Coviu platform.
- NOTE: Your chosen login email domain at the end of the string is the email domain your staff use to access SSO. You may have set up configurations for multiple email domains.
- Click Register
- You should now have a new application registration available.
-
In order to configure your application within Coviu, you will need to provide the URL to your Federation Metadata document. This can be found under the Endpoints option in your application configuration.
-
This Federation Metadata Document URL should be entered into the Coviu SSO self-configuration portal as described in the sections below. It is used to extract the SSO Sign on URL, the entity ID, and certificates needed to perform SSO.
-
You will also need your Application (client) ID which is the issuer ID.
How do I get to the self-help SSO Configuration interface?
If you do not have access to the Coviu platform as an administrator, contact your Coviu Application Owner or your internal project manager. You will need access as a platform administrator to populate the SSO self-configuration portal and activate SSO.
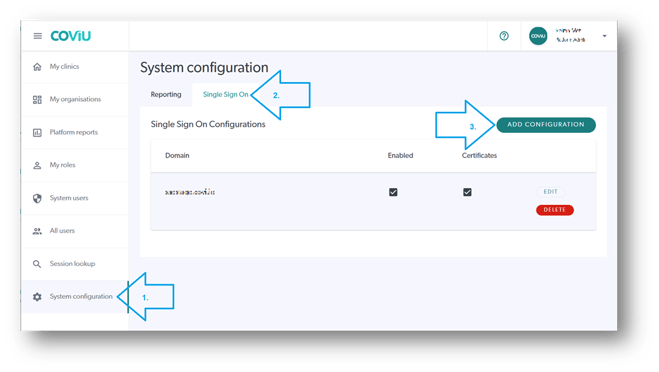
Log into Coviu as you normally would:
- If you are already in the platform and on the platform dashboard shown below, click System Configuration in the left hand menu.
- Click the Single Sign On tab.
- Click Add Configuration.
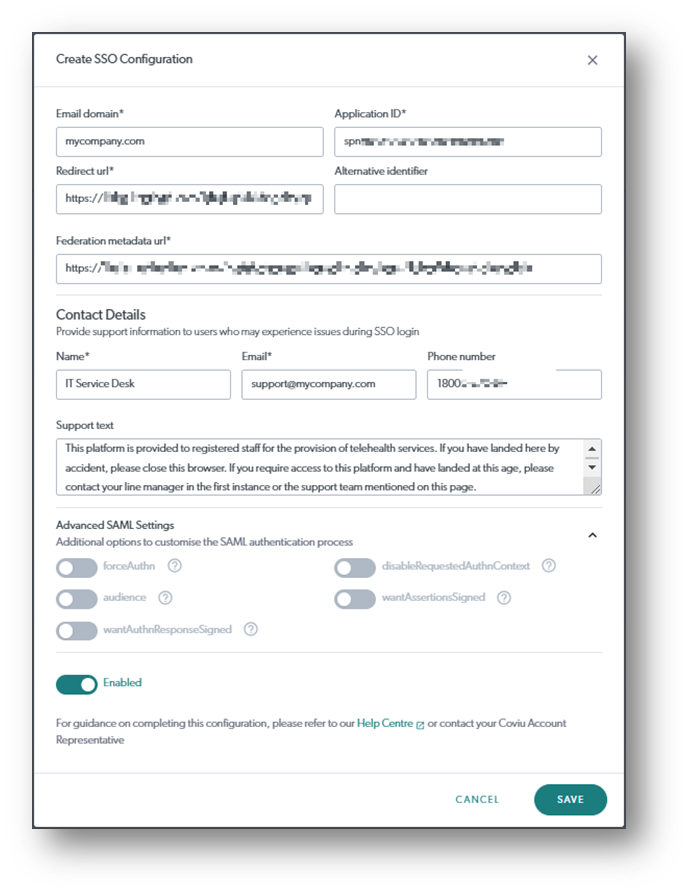
- On the Create SSO Configuration interface (see below screen capture), add the required details.
- Ticking the Enabled option will make your configuration go live so proceed with caution.
- A go-live date is usually planned with the project team
- It is generally recommended to get SSO implemented prior to having all clinicians added to the platform.
- Save the configuration when done. If you have chosen Enabled, then your system should be ready to go.
What configuration items will you need for the Interface?
The details you enter into the Coviu SSO self-help Configuration interface (below) are those details that come from creating the Coviu application in your IdP and from the resulting federation metaData XML file. The below table outlines the fields required in our SSO self-help portal:
| Email domain |
If you have multiple email domains accessing the platform, you will need to create an SSO configuration for each domain. |
| Application (client) ID |
Taken from your IdP portal. Could be referred to as Application ID, Entity ID or Client ID. in the format of spn:xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx |
| Redirect URL | Extracted from your federation metadata XML file Usually toward the bottom of your XML file e.g https://login.microsoftonline.com/xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx/saml2 |
|
Alternative Identifier (is not mandatory) |
Add if required |
| Federation metadata URL | As per your Azure application creation |
| Contact Details |
Add your support contact details and support text. This is for any staff member who arrives at your platform login screen but has not yet been assigned to a clinic. The Support details should point the user at an administrator who can assist them with the right access. The details could be for your Coviu Application Owner, your SSO System Administrator or your IT Service Desk for example. |
|
Advanced SAML Settings |
|
| forceAuthn |
Why would I turn this on? When forceAuthn is enabled, the user will have to enter their SSO username and password every time, even when they have a valid session |
| disableRequestedAuthnContext |
Why would I turn this on? The library we use for SAML authentication requires PasswordProtectedTransport(PPT) to be used. Some ADFS configurations may be set up in a way that does not support PPT and will use Windows Federation Authentication Protocol. This will result in authentication context errors and the user will not be able to log in. In that case, turning this toggle on, will help the issue. |
| wantAuthnResponseSigned |
When enabled, the SAML authentication response must be signed by the IDP. |
| disableRequestedAuthContext |
The authentication context is disabled so that the IDP determines the method of authentication. |
| wantAssertionsSigned |
When enabled, the SAML assertions must be signed by the IDP. |
|
Save your settings and turn SSO on! |
|
| Save | Click save to save the configuration (this does not turn SSO on unless you have toggled the Enable toggle to "on".) |
| Enabled toggle | Used to turn SSO on/off (handy for out of hours testing) |
FAQs for your SSO Administrator
- Do we integrate with other SSO technologies?
- Information on integrating with on-prem ADFS can be found here.
- If your organisation uses another means for SSO, let us know. Register your interest with your Coviu account representative.
- Do we support SAML 2.0?
- Yes, SAML 2.0 is the protocol we support at the moment.
- Advanced SAML Settings explained
- forceAuthn - when forceAuthn is enabled, the user will have to enter SSO username and password every time, even when they have a valid session
- disableRequestedAuthnContext - The library we use for SAML authentication requires PasswordProtectedTransport(PPT) to be used. Some ADFS configurations may be set up in a way that does not support PPT and will use Windows Federation Authentication Protocol. This will result in authentication context errors and the user will not be able to log in. In that case, turning this toggle on, will help the issue.
- Is our product (Coviu) listed in the Azure Marketplace/Gallery?
- No. Not at this stage.
- Authentication state?
- Forms based.
- Do we require Microsoft ADFS 3.0 to encrypt assertions to protect data leakage of sensitive information passed back to Coviu during logon?
- We don't support this extra layer of encryption at the moment.
- Do we require the Microsoft ADFS 3.0 to sign their assertions?
- Yes, we validate the signatures when we receive a request/response from Microsoft ADFS 3.0.
FAQs for the end user
- When we turn on SSO, will staff be able to access Coviu from our normal platform URL?
- Yes. Staff would still log into Coviu from the link they have been using or have been provided.
- If the organisation has an SSO portal, the organisation's SSO administrator may need to provide details on how to access the Coviu platform from the portal.
- If staff can access it from the normal link, will the password field still display?
- No. If the staff member has already signed in to SSO (their portal), then they will pass straight through to Coviu.
- Will the password in Coviu automatically change to match their SSO password?
- No. Staff would use their corporate SSO credentials. If they have not logged in to SSO, they would be redirected to their SSO login page and then back to Coviu.
- Further, Coviu could never know what the SSO password is and passwords would not be shared across platforms.
Who do I contact for Support?
- You can contact your Coviu account manager directly, alternatively,
- You can contact us through one of the options available here.
